Blogs
The Vital Role of Physical Security in Schools
In today’s world, ensuring the safety of students and staff is more important than ever. To create secure learning environments, educational institutions are increasingly turning to advanced security solutions.
Boost Security, Operational Efficiency, and Savings with Advanced Access Control Systems
In today’s evolving security landscape, advanced access control systems are indispensable for safeguarding facilities. These systems not only prevent unauthorized entry but also offer a comprehensive solution to manage access across various areas.
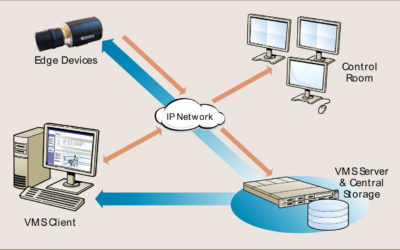
March Network – Shadow Archiving in Video Surveillance Systems
You may have considered making the transition to cloud video surveillance, but you’ve hesitated for one reason: you need 24/7 surveillance with NO downtime – and that includes network outages. While it’s true that even the most reliable networks cannot guarantee 100 percent uptime, that’s no reason to avoid making the transition to cloud-based video security.
March Network – Networked Video Security for Banks & Credit Unions
While computers and the internet have made many aspects of business and commerce easier, technology advances have not been entirely beneficial. Data breaches and catastrophic data loss are a painful reality for too many companies of all sizes.
Reliable City-Wide Video Surveillance from Access Technologies
As security experts will tell you, video surveillance systems are the platform to protect our most important investments. In our local communities, this means protecting citizens, government property, and monitoring remote installations…
The Importance of Maintenance Contracts for Systems
Access Technologies provides advanced technological solutions for businesses, government organizations, educational institutions, and utilities. Each entity that we work with has different needs, and as systems become increasingly more complex, proper maintenance is critical…
Get in Touch
Want to know more about how technology can help your business? Get in touch with our expert technicians.